This quarter, threat actors successfully leveraged trusted third-party suppliers to attack intended victim organizations. The compromise of identity provider Okta resulted in risk exposure for 134 of its customers and resulted in three subsequent compromises. Since the successful SolarWinds attack in 2020 that used a third-party supplier compromise to target victims, cyber attacks which exploit the trust relationship with third-party suppliers have soared. These multi-stage attacks were once rare due to their complexity and lengthy timelines, but well-funded threat actors now have the resources to execute them. Additionally, nation state actors' collaboration with cyber criminals has led to the proliferation of sophisticated tools and techniques in the cyber crime ecosystem.
Cradlepoint’s zero trust solutions can provide protection against these increasingly well-funded threat actors and sophisticated attacks. Our security model is built on a modern foundation of zero trust, top to bottom. The following cyber-crime threats from this quarter exemplify how Cradlepoint can mitigate the risk from third-party suppliers, 'bring your own device' (BYOD), phishing, and malicious websites.
Web browser vulnerability enables one-click compromise
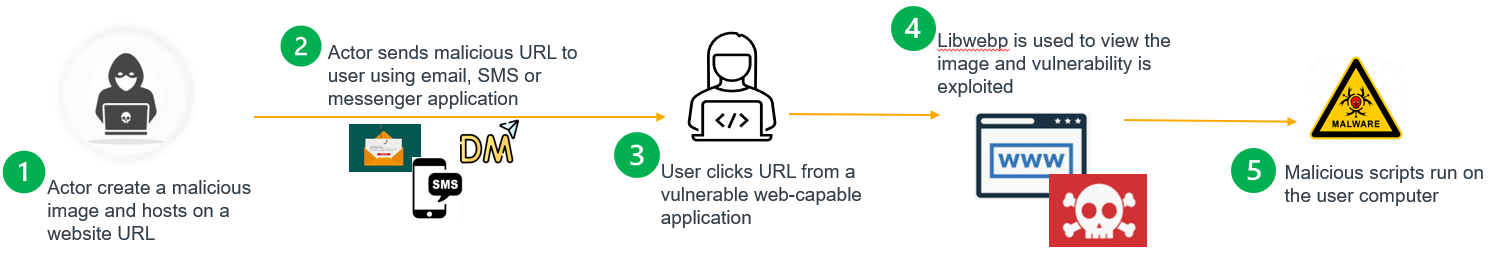
In September, security researchers at Citizen Lab revealed a web-based exploit requiring only that a user view a malicious image in a vulnerable web browser or browser-based application to launch a malware attack (see Figure 1). The malware exploit leveraged a buffer overflow vulnerability in “libwebp”, a widely-used open-source software for web-capable applications, including Chrome, Edge, Firefox and over seven hundred applications with embedded web browsers. Remote Browser Isolation (RBI) and Web Application Isolation (WAI) effectively protect web browsers and web apps from zero-day malware.
Figure 1
WAI protects internal corporate applications from third-party contractors and BYOD employees. WAI ensures robust protection against threats by rendering apps in a secure cloud environment, with features like blocking file transfers, malware sanitization, and read-only mode. Conversely, using virtualized browser instances, RBI protects users from local browser vulnerabilities, preventing interactions with malicious content, such as attacks leveraging the libwebp vulnerability.
Find more details from Isosceles and Akamai.
Unmanaged end user computing (EUC) devices frequently used for initial access attacks
Microsoft's Digital Defense Report reported that 80-90% of successful ransomware attacks involved unmanaged EUDs. Unmanaged EUDs include desktop computers, laptops, tablets, smartphones, and similar computing devices that lack known security controls.
Other highlights from the report include:
- 70% of organizations targeted by “human operated ransomware” had less than 500 employees.
- The education and manufacturing sectors were popular targets of ransomware operators.
- The top 4 observed ransomware variants were Magniber, Lockbit, Hive, and BlackCat.
The primary reason that threat actors target organizations with less than 500 employees is these companies often have less sophisticated security controls compared to larger companies. However businesses require Lean-IT to be more agile than ever. They roll out sites faster, use temporary sites more frequently, connect to the network in vehicles and through kiosks, and have employees that work anywhere. This is why thousands of companies around the globe are adopting more flexible connectivity like Wireless WAN.
NetCloud Exchange (NCX) architecture, with Connect-and-go zero trust, enhances WAN security by replacing complex VPNs and specifically mitigates the risk of ransomware lateral movement from unmanaged EUDs.
For more details, read the 2023 Microsoft Digital Defense Report.
QakBot most prevalent malware dropper
CISA's updated Stop Ransomware Guide emphasized blocking malicious URLs in phishing emails and implementing a zero trust architecture to prevent initial access attacks. QakBot, the most prevalent "dropper" malware, initiates ransomware attacks by using convincing email language to prompt users to click on a download URL. The dropper malware then downloads ransomware to launch an attack inside the organization's network (see Figure 2).
Figure 2
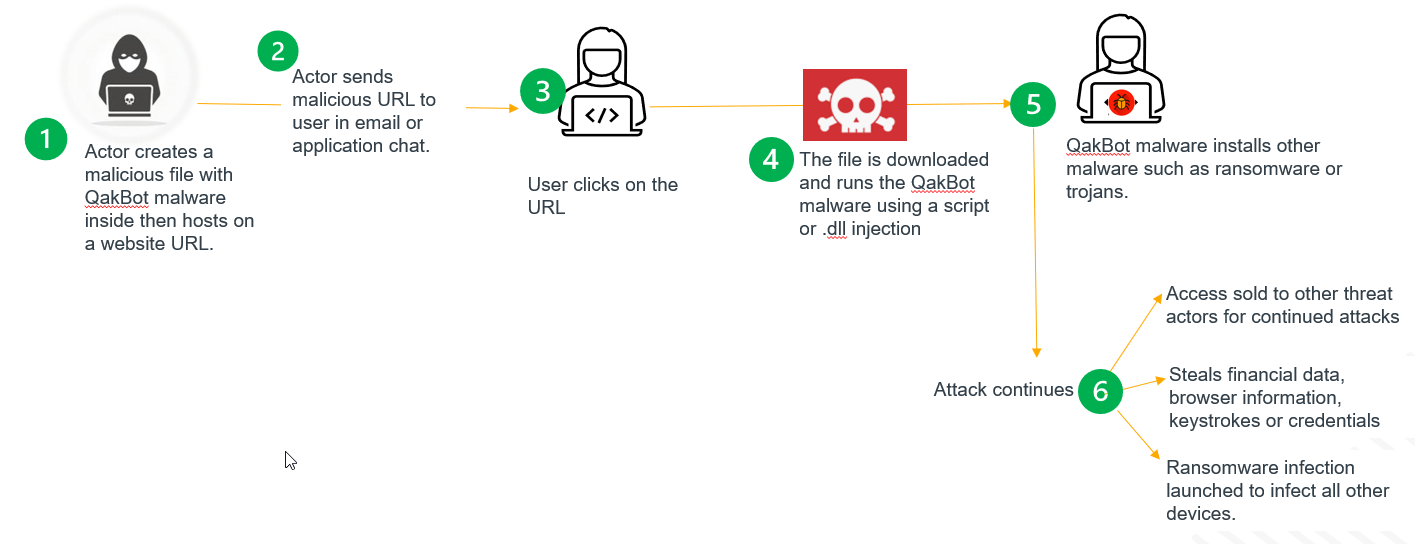
In October 2023, global law enforcement efforts successfully dismantled QakBot's online infrastructure and cleaned thousands of compromised systems. However, there's a high likelihood that other threat actors will establish a new infrastructure due to QakBot's effectiveness.
Cradlepoint’s Remote Browser Isolation (RBI) can potentially stop the delivery of dropper software, making it an effective defense against common initial access vectors in ransomware campaigns. File downloads are blocked, or sanitized by the Content Disarm and Reconstruction (CDR) feature before download by removing malicious code from the file. A ransomware infection costs millions, as per IBM's 2023 Data Breach Report. Implementing CISA guidelines, with tools like RBI, can help businesses avoid ransomware infections.
For more details, visit the CISA Stop Ransomware Guide and the Krebson Security site.
Threat actors upgrade IoT malware for exploitation and post-comprise activities
Compromising IoT devices to expand botnets continues to be a priority for threat actors. Botnets are profitable and usually do not attract attention from law enforcement. Mirai malware is favored by threat actors due to its ease of adding functionality and relatively high success rate of IoT devices. Security researchers at NSFOCUS detected three new variants of the Mirai botnet: hailBot, kiraiBot and catDDoS. The added functionality in the new variants is to impede detection of the exploit and post-compromise activity.
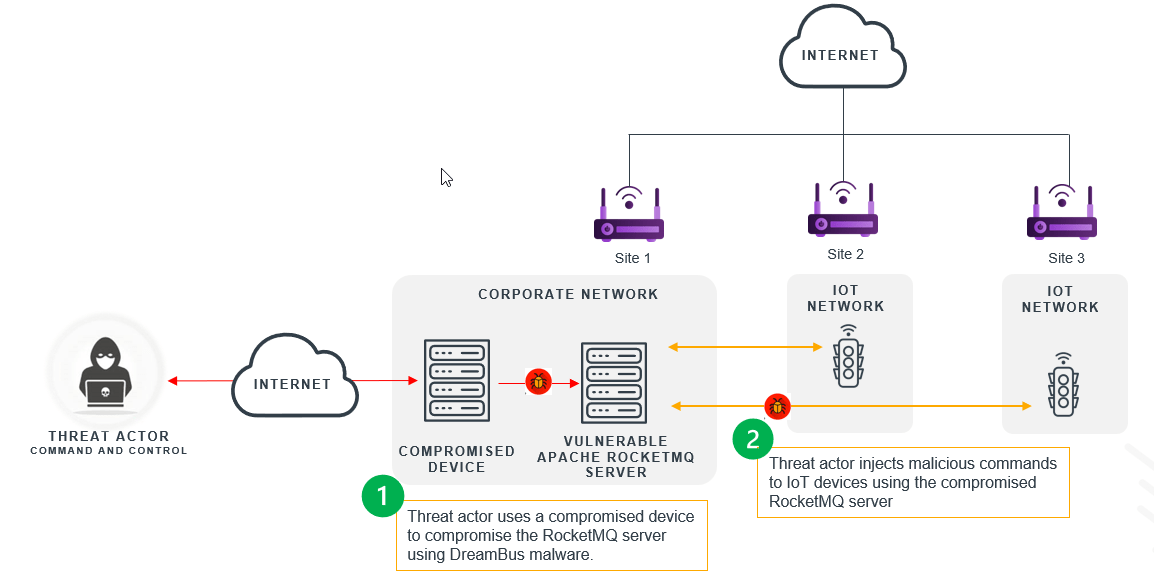
Additionally, DreamBus malware targeted Apache RocketMQ server, commonly used for managing ICS and IoT devices. A successful compromise may impact device availability and potentially extend the scope of attacks to interconnected networks (see Figure 3). A threat actor, a malicious insider, or an infected IoT device can be used to deploy the DreamBus malware to other systems -- like an EUD. At the time of publication, over twenty five hundred devices running Apache RocketMQ were internet facing.
Figure 3